Centos8 Curl报错SSL certificate problem: EE certificate key too weak
今天用Centos8做底包调试新的包源(私有包源),dnf安装包一直失败(以前是用yum,centos8已经换成了dnf,yum作为dnf的软链接还可以继续使用),报错如下:
Curl error (60): Peer certificate cannot be authenticated with given CA certificates for
https://xxxx/repomd.xml [SSL certificate problem: EE certificate key too weak]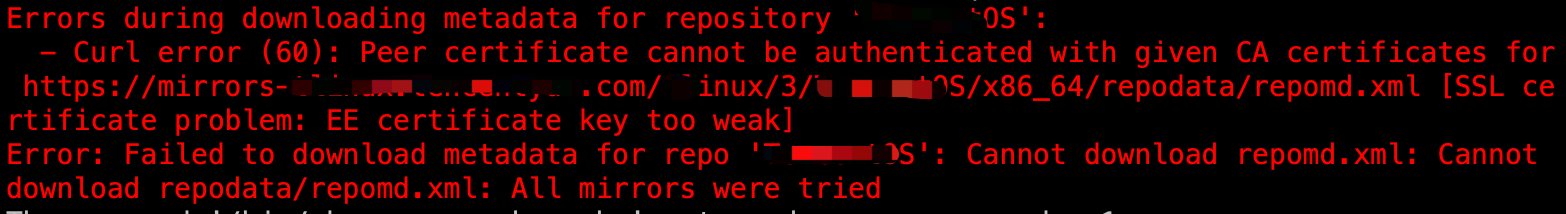
问题原因
一开始以为是证书问题,更新证书无果,最后还是Google大法找到一个解决方案。原因是Centos8升级了安全策略级别,默认策略中关闭了对TSL1.0,TSL1.1协议的认可,而我们的包源站点还用的是旧版本。
解决方案
修改安全策略,启用TSL低版本协议
# 先查看一下当前策略是否DEFAULT
update-crypto-policies --show
# 把策略修改成 LEGACY
update-crypto-policies --set LEGACY延伸
附上几个策略的详细描述
| 级别 | 描述 |
|---|---|
| DEFAULT | The default system-wide cryptographic policy level offers secure settings for current threat models. It allows the TLS 1.2 and 1.3 protocols, as well as the IKEv2 and SSH2 protocols. The RSA keys and Diffie-Hellman parameters are accepted if they are at least 2048 bits long. |
| LEGACY | This policy ensures maximum compatibility with Red Hat Enterprise Linux 5 and earlier; it is less secure due to an increased attack surface. In addition to the DEFAULT level algorithms and protocols, it includes support for the TLS 1.0 and 1.1 protocols. The algorithms DSA, 3DES, and RC4 are allowed, while RSA keys and Diffie-Hellman parameters are accepted if they are at least 1023 bits long. |
| FUTURE | A conservative security level that is believed to withstand any near-term future attacks. This level does not allow the use of SHA-1 in signature algorithms. It allows the TLS 1.2 and 1.3 protocols, as well as the IKEv2 and SSH2 protocols. The RSA keys and Diffie-Hellman parameters are accepted if they are at least 3072 bits long. |
| FIPS | A policy level that conforms with the FIPS 140-2 requirements. This is used internally by the fips-mode-setup tool, which switches the RHEL system into FIPS mode. |